| How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank. |
|
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
|
CyberOps Associate (Version 1.0) – CyberOps Associate (200-201) Certification Practice Exam
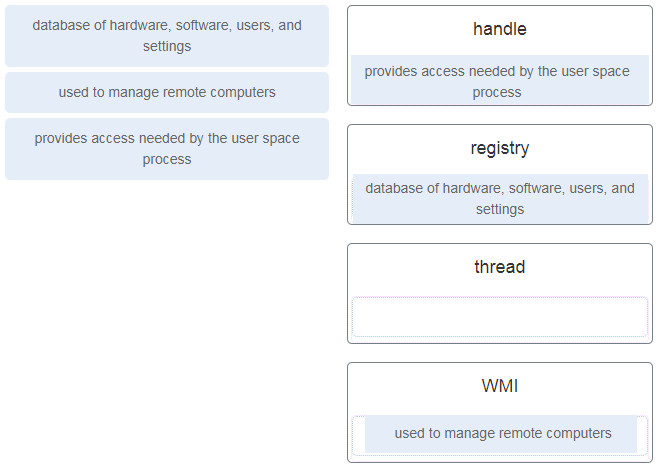
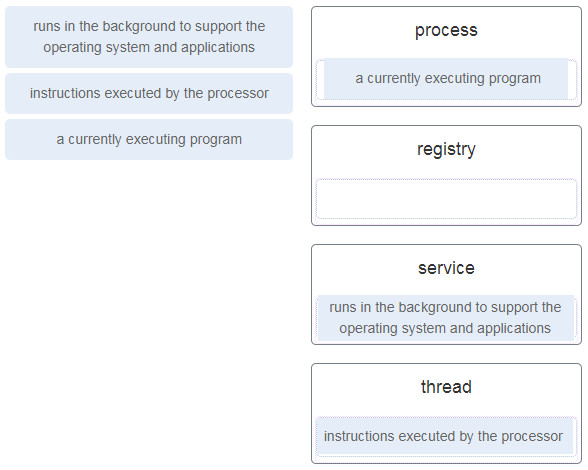
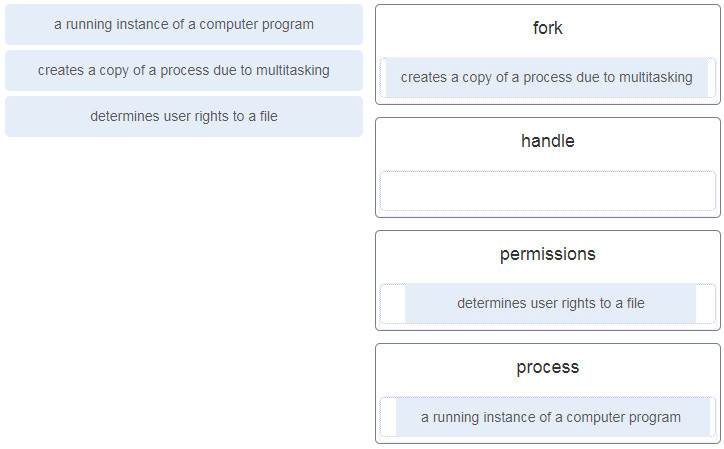
1. Match the definition to the Microsoft Windows term. (Not all options are used.)
Case 2
2. What are two motivating factors for nation-state sponsored threat actors? (Choose two.)
- industrial espionage
- showing off their hacking skill
- disruption of trade or infrastructure
- social or personal causes
- financial gain
Explanation: Nation-state threat actors are not typically interested or motivated by financial gain. They are primarily involved in corporate espionage or disrupting international trade or critical infrastructure.
3. Match the description to the Linux term. (Not all options are used.)
Other case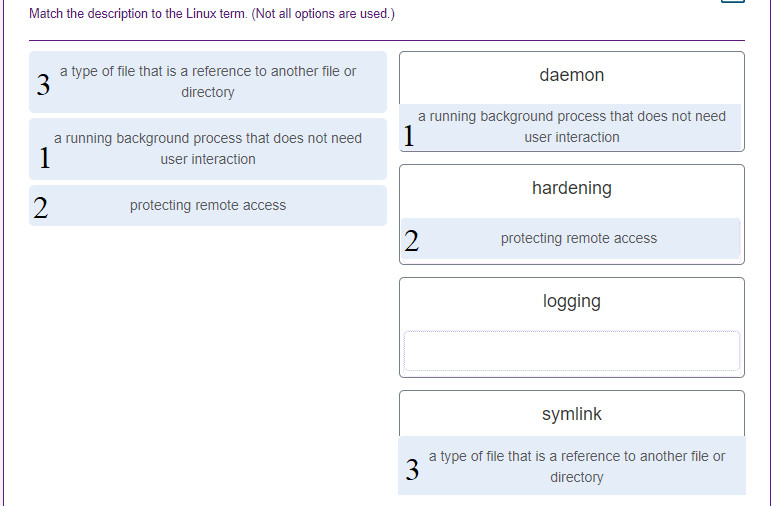
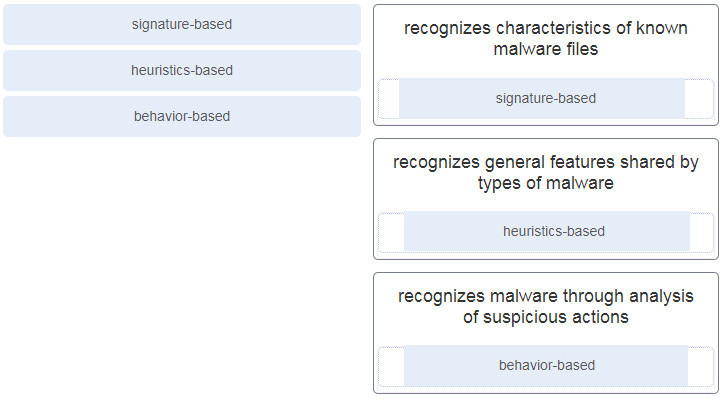
4. Match the antimalware approach to the description.
5. Which type of data is used by Cisco Cognitive Intelligence to find malicious activity that has bypassed security controls, or entered through unmonitored channels, and is operating inside an enterprise network?
- statistical
- session
- alert
- transaction
Explanation: Cisco Cognitive Intelligence utilizes statistical data for statistical analysis in order to find malicious activity that has bypassed security controls, or entered through unmonitored channels (including removable media), and is operating inside the network of an organization.
6. Which type of evasion technique splits malicious payloads into smaller packets in order to bypass security sensors that do not reassemble the payloads before scanning them?
- pivoting
- traffic fragmentation
- protocol-level misinterpretation
- traffic insertion
Explanation: In order to keep the malicious payload from being recognized by security sensors, such as IPS or IDS, perpetrators fragment the data into smaller packets.These fragments can be passed by sensors that do not reassemble the data before scanning.
7. Which type of cyber attack is a form of MiTM in which the perpetrator copies IP packets off the network without modifying them?
- compromised key
- eavesdropping
- denial-of-service
- IP spoofing
Explanation: An eavesdropping attack is a form of man-in-the-middle in which the perpetrator just reads or copies IP packets off the network but does not alter them.
8. Which is an example of social engineering?
- an anonymous programmer directing a DDoS attack on a data center
- an unidentified person claiming to be a technician collecting user information from employees
- a computer displaying unauthorized pop-ups and adware
- the infection of a computer by a virus carried by a Trojan
Explanation: A social engineer attempts to gain the confidence of an employee and convince that person to divulge confidential and sensitive information, such as usernames and passwords. DDoS attacks, pop-ups, and viruses are all examples of software based security threats, not social engineering.
9. Which component is a pillar of the zero trust security approach that focuses on the secure access of devices, such as servers, printers, and other endpoints, including devices attached to IoT?
- workflows
- workloads
- workplace
- workforce
Explanation: The workplace pillar focuses on secure access for any and all devices, including devices on the internet of things (IoT), which connect to enterprise networks, such as user endpoints, physical and virtual servers, printers, cameras, HVAC systems, kiosks, infusion pumps, industrial control systems, and more.
10. A security analyst is reviewing information contained in a Wireshark capture created during an attempted intrusion. The analyst wants to correlate the Wireshark information with the log files from two servers that may have been compromised. What type of information can be used to correlate the events found in these multiple data sets?
- ISP geolocation data
- IP five-tuples
- logged-in user account
- ownership metadata
Explanation: The source and destination IP address, ports, and protocol (the IP five-tuples) can be used to correlate different data sets when analyzing an intrusion.
11. A security analyst is investigating a cyber attack that began by compromising one file system through a vulnerability in a custom software application. The attack now appears to be affecting additional file systems under the control of another security authority. Which CVSS v3.0 base exploitability metric score is increased by this attack characteristic?
- privileges required
- scope
- attack complexity
- user interaction
Explanation: The scope metric is impacted by an exploited vulnerability that can affect resources beyond the authorized privileges of the vulnerable component or that are managed by a different security authority.
12. Which regular expression would match any string that contains 4 consecutive zeros?
- {0-4}
- [0-4]
- 0{4}
- ^0000
Explanation: The regular expression 0{4} matches any string that contains 4 repetitions of zero or 4 consecutive zeros.
13. Refer to the exhibit. Which technology generated the event log?
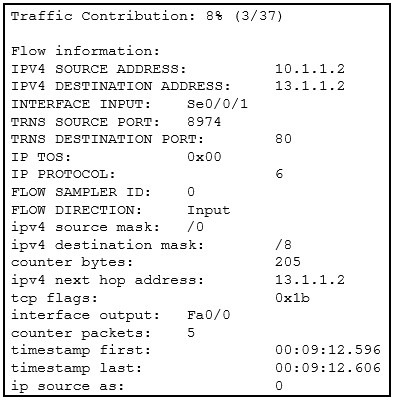
- Wireshark
- Netflow
- web proxy
- syslog
Explanation: The source of the output is Netflow.
14. Refer to the exhibit. A security specialist is using Wireshark to review a PCAP file generated by tcpdump . When the client initiated a file download request, which source socket pair was used?
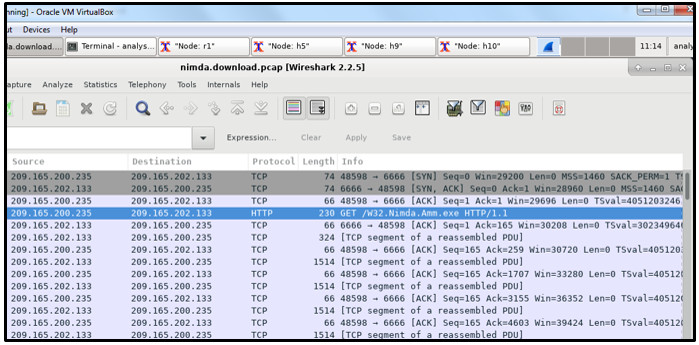
- 209.165.202.133:48598
- 209.165.202.133:6666
- 209.165.200.235:6666
- 209.165.200.235:48598
Explanation: The combination of the source IP address and source port number, or the destination IP address and destination port number, is known as a socket. A socket is shown as the IP address and associated port number with a colon in between the two (IP_address:port_number).
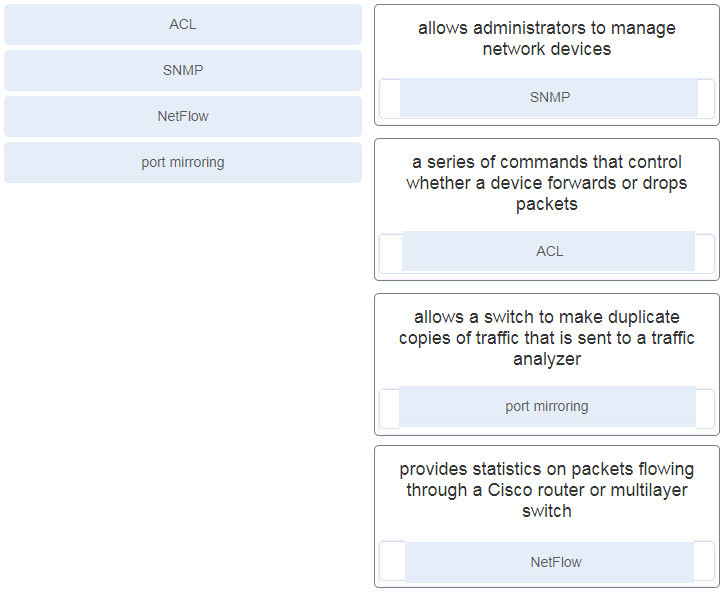
15. Match the security service with the description.
16. Using Tcpdump and Wireshark, a security analyst extracts a downloaded file from a pcap file. The analyst suspects that the file is a virus and wants to know the file type for further examination. Which Linux command can be used to determine the file type?
- file
- tail
- nano
- ls -l
Explanation: The Linux file command can be used to determine a file type, such as whether it is executable, ASCII text, or zip.
17. Match the IPS alarm with the description.
18. What is a feature of an IPS?
- It can stop malicious packets.
- It is deployed in offline mode.
- It has no impact on latency.
- It is primarily focused on identifying possible incidents.
Explanation: An advantage of an intrusion prevention systems (IPS) is that it can identify and stop malicious packets. However, because an IPS is deployed inline, it can add latency to the network.
19. Which three fields are found in both the TCP and UDP headers? (Choose three.)
- window
- checksum
- options
- sequence number
- destination port
- source port
Explanation: The UPD header has four fields. Three of these fields are in common with the TCP header. These three fields are the source port, destination port, and checksum.
20. What will match the regular expression ^83?
- any string that includes 83
- any string that begins with 83
- any string with values greater than 83
- any string that ends with 83
Explanation: The expression ^83 indicates any string that begins with 83 will be matched.
21. What is a key difference between the data captured by NetFlow and data captured by Wireshark?
- NetFlow provides transaction data whereas Wireshark provides session data.
- NetFlow data is analyzed by tcpdump whereas Wireshark data is analyzed by nfdump.
- NetFlow collects metadata from a network flow whereas Wireshark captures full data packets.
- NetFlow data shows network flow contents whereas Wireshark data shows network flow statistics.
Explanation: Wireshark captures the entire contents of a packet. NetFlow does not. Instead, NetFlow collects metadata, or data about the flow.
22. Which three IPv4 header fields have no equivalent in an IPv6 header? (Choose three.)
- flag
- identification
- TTL
- fragment offset
- version
- protocol
Explanation: Unlike IPv4, IPv6 routers do not perform fragmentation. Therefore, all three fields supporting fragmentation in the IPv4 header are removed and have no equivalent in the IPv6 header. These three fields are fragment offset, flag, and identification. IPv6 does support host packet fragmentation through the use of extension headers, which are not part of the IPv6 header.
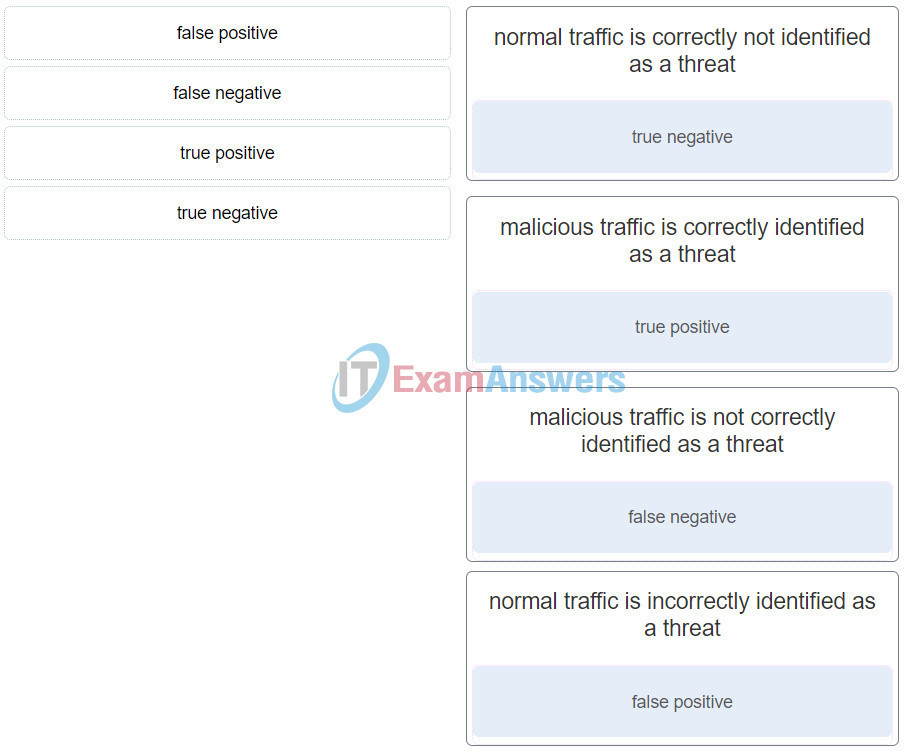
23. What classification is used for an alert that correctly identifies that an exploit has occurred?
- false negative
- false positive
- true positive
- true negative
Explanation: A true positive occurs when an IDS and IPS signature is correctly fired and an alarm is generated when offending traffic is detected.
24. Match the NIST incident response life cycle phase with the description.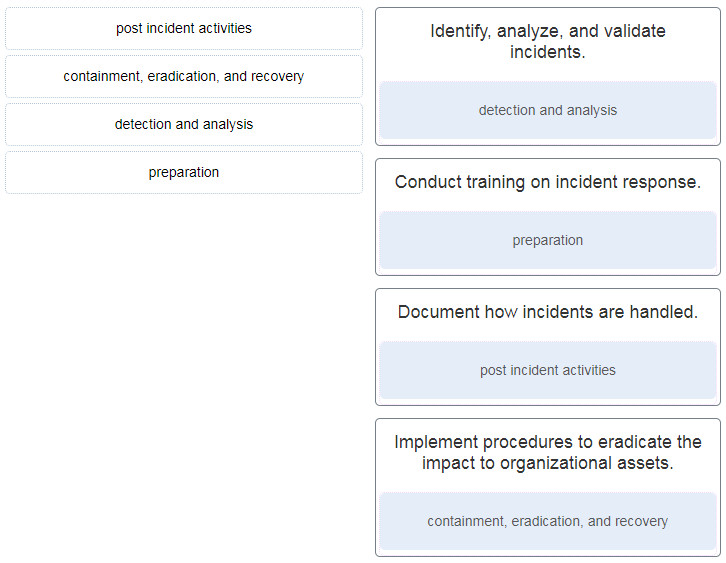
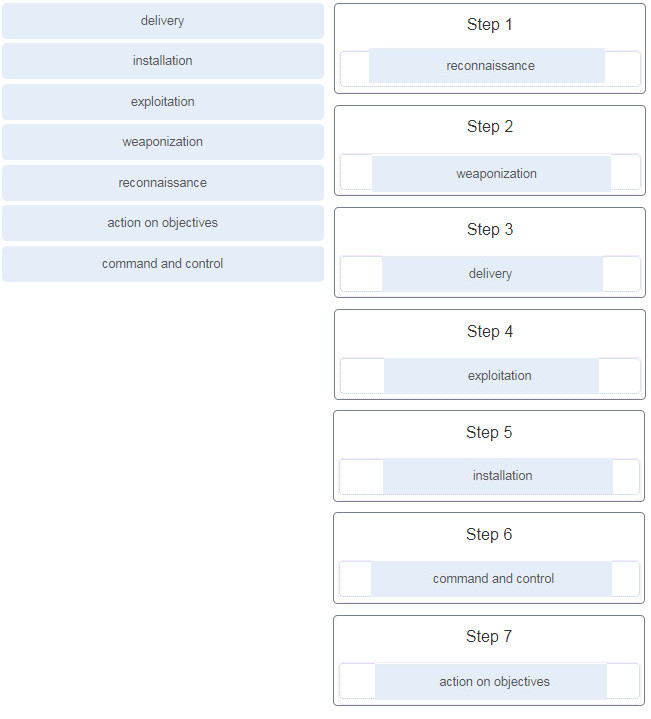
25. Place the seven steps defined in the Cyber Kill Chain in the correct order.
26. During the detection and analysis phase of the NIST incident response process life cycle, which sign category is used to describe that an incident might occur in the future?
- attrition
- impersonation
- precursor
- indicator
Explanation: There are two categories for the signs of an incident:
- Precursor – a sign that an incident might occur in the future
- Indicator – a sign that an incident might already have occurred or is currently occurring
27. According to the Cyber Kill Chain model, after a weapon is delivered to a targeted system, what is the next step that a threat actor would take?
- action on objectives
- exploitation
- weaponization
- installation
Explanation: The Cyber Kill Chain specifies seven steps (or phases) and sequences that a threat actor must complete to accomplish an attack:
- Reconnaissance – The threat actor performs research, gathers intelligence, and selects targets.
- Weaponization – The threat actor uses the information from the reconnaissance phase to develop a weapon against specific targeted systems.
- Delivery – The weapon is transmitted to the target using a delivery vector.
- Exploitation – The threat actor uses the weapon delivered to break the vulnerability and gain control of the target.
- Installation – The threat actor establishes a back door into the system to allow for continued access to the target.
- Command and Control (CnC) – The threat actor establishes command and control (CnC) with the target system.
- Action on Objectives – The threat actor is able to take action on the target system, thus achieving the original objective.
28. A company is applying the NIST.SP800-61 r2 incident handling process to security events. What are two examples of incidents that are in the category of precursor? (Choose two.)
- multiple failed logins from an unknown source
- log entries that show a response to a port scan
- an IDS alert message being sent
- a newly-discovered vulnerability in Apache web servers
- a host that has been verified as infected with malware
Explanation: As an incident category, the precursor is a sign that an incident might occur in the future. Examples of precursors are log entries that show a response to a port scan or a newly-discovered vulnerability in web servers using Apache.
29. A network administrator is creating a network profile to generate a network baseline. What is included in the critical asset address space element?
- the time between the establishment of a data flow and its termination
- the TCP and UDP daemons and ports that are allowed to be open on the server
- the IP addresses or the logical location of essential systems or data
- the list of TCP or UDP processes that are available to accept data
Explanation: A network profile should include some important elements, such as the following:
Total throughput – the amount of data passing from a given source to a given destination in a given period of time
Session duratio n – the time between the establishment of a data flow and its termination
Ports used – a list of TCP or UDP processes that are available to accept data
Critical asset address space – the IP addresses or the logical location of essential systems or data
30. Which NIST-defined incident response stakeholder is responsible for coordinating incident response with other stakeholders and minimizing the damage of an incident?
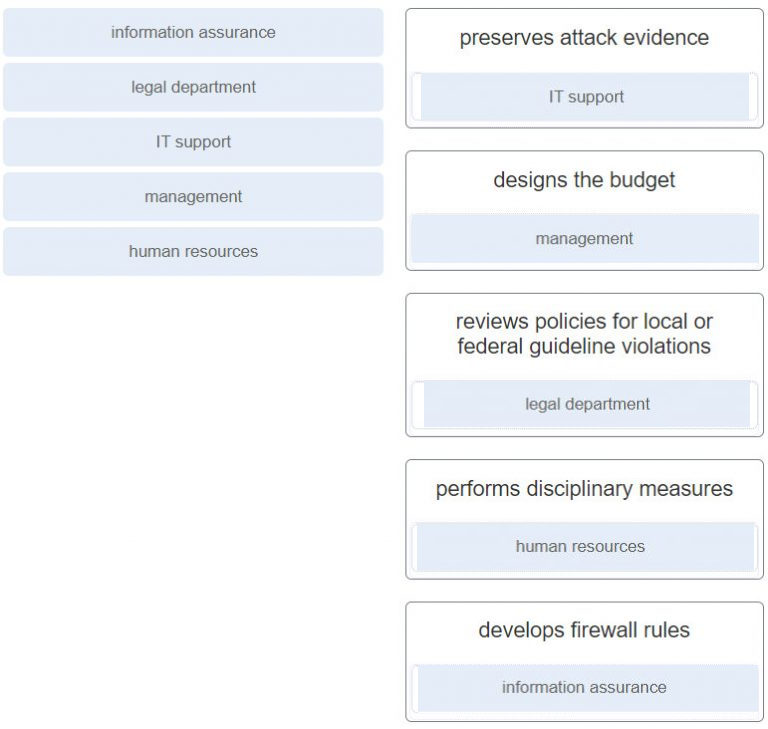
- human resources
- IT support
- the legal department
- management
Explanation: The management team creates the policies, designs the budget, and is in charge of staffing all departments. Management is also responsible for coordinating the incident response with other stakeholders and minimizing the damage of an incident.
31. What is defined in the policy element of the NIST incident response plan?
- how to handle incidents based on the mission and functions of an organization
- a roadmap for updating the incident response capability
- the metrics used for measuring incident response capability in an organization
- how the incident response team of an organization will communicate with organization stakeholders
Explanation: The policy element of the NIST incident response plan details how incidents should be handled based on the mission and function of the organization.
32. What is the responsibility of the human resources department when handing a security incident as defined by NIST?
- Review the incident policies, plans, and procedures for local or federal guideline violations.
- Perform disciplinary actions if an incident is caused by an employee.
- Coordinate the incident response with other stakeholders and minimize the damage of an incident.
- Perform actions to minimize the effectiveness of the attack and preserve evidence.
Explanation: The human resources department may be called upon to perform disciplinary measures if an incident is caused by an employee.
33. What is the benefit of a defense-in-depth approach?
- All network vulnerabilities are mitigated.
- The need for firewalls is eliminated.
- Only a single layer of security at the network core is required.
- The effectiveness of other security measures is not impacted when a security mechanism fails.
Explanation: The benefit of the defense-in-depth approach is that network defenses are implemented in layers so that failure of any single security mechanism does not impact other secuirty measures.
34. Which type of analysis relies on predefined conditions and can analyze applications that only use well-known fixed ports?
- statistical
- deterministic
- log
- probabilistic
Explanation: Deterministic analysis uses predefined conditions to analyze applications that conform to specification standards, such as performing a port-based analysis.
35. Which type of analysis relies on different methods to establish the likelihood that a security event has happened or will happen?
- deterministic
- statistical
- log
- probabilistic
Explanation: Probabilistic methods use powerful tools to create a probabilistic answer as a result of analyzing applications.
36. Which access control model allows users to control access to data as an owner of that data?
- mandatory access control
- nondiscretionary access control
- discretionary access control
- attribute-based access control
Explanation: In the discretionary access control (DAC) model, users can control access to data as owners of the data.
37. What are the three impact metrics contained in the CVSS 3.0 Base Metric Group? (Choose three.)
- confidentiality
- remediation level
- integrity
- attack vector
- exploit
- availability
Explanation: The Common Vulnerability Scoring System (CVSS) is a vendor-neutral, industry standard, open framework for weighing the risks of a vulnerability using a variety of metrics. CVSS uses three groups of metrics to assess vulnerability, the Base Metric Group, Temporal Metric Group, and Environmental Metric Group. The Base Metric Group has two classes of metrics (exploitability and impact). The impact metrics are rooted in the following areas: confidentiality, integrity, and availability.
38. Which access control model applies the strictest access control and is often used in military and mission critical applications?
- discretionary
- mandatory
- nondiscretionary
- attribute-based
Explanation: Military and mission critical applications typically use mandatory access control which applies the strictest access control to protect network resources.
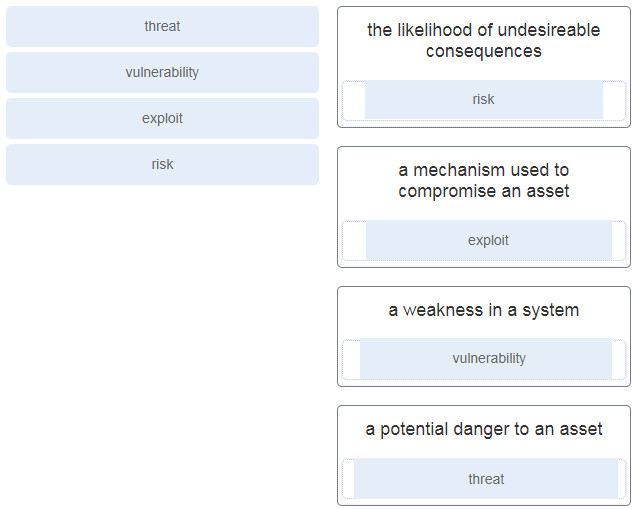
39. Match the security concept to the description.
40. What is the principle behind the nondiscretionary access control model?
- It applies the strictest access control possible.
- It allows access decisions to be based on roles and responsibilities of a user within the organization.
- It allows users to control access to their data as owners of that data.
- It allows access based on attributes of the object be to accessed.
Explanation: The nondiscretionary access control model used the roles and responsibilities of the user as the basis for access decisions.
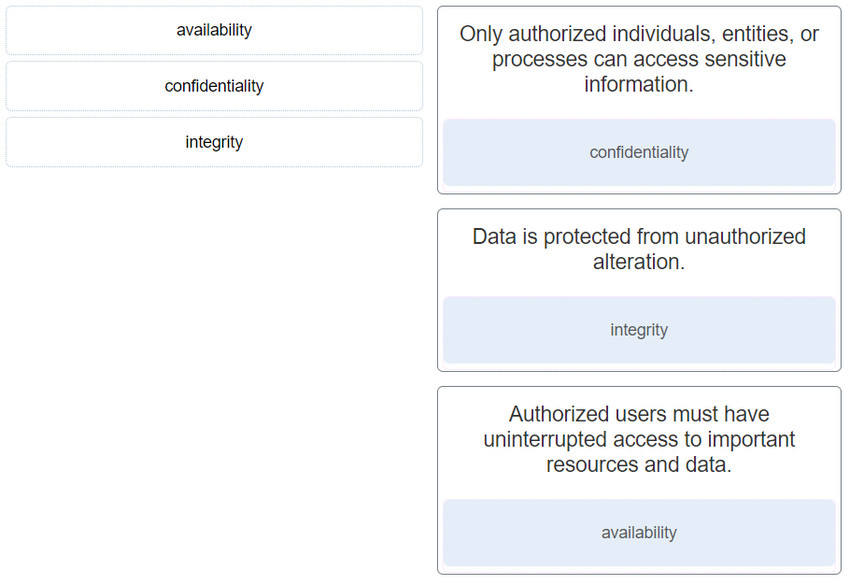
41. Match the information security component with the description.
42. Which attack is integrated with the lowest levels of the operating system of a host and attempts to completely hide the activities of the threat actor on the local system?
- rootkit
- traffic insertion
- traffic substitution
- encryption and tunneling
Explanation: A rootkit is a complex attack tool and it integrates with the lowest levels of the operating system. The goal of the rootkit is to completely hide the activities of the threat actor on the local system.
43. Which tool captures full data packets with a command-line interface only?
- nfdump
- NBAR2
- tcpdump
- Wireshark
Explanation: The command-line tool tcpdump is a packet analyzer. Wireshark is a packet analyzer with a GUI interface.
44. To which category of security attacks does man-in-the-middle belong?
- DoS
- access
- reconnaissance
- social engineering
Explanation: With a man-in-the-middle attack, a threat actor is positioned in between two legitimate entities in order to read, modify, or redirect the data that passes between the two parties.
45. What is an example of a local exploit?
- Port scanning is used to determine if the Telnet service is running on a remote server.
- A threat actor performs a brute force attack on an enterprise edge router to gain illegal access.
- A buffer overflow attack is launched against an online shopping website and causes the server crash.
- A threat actor tries to gain the user password of a remote host by using a keyboard capture software installed on it by a Trojan.
Explanation: Vulnerability exploits may be remote or local. In a local exploit, the threat actor has some type of user access to the end system, either physically or through remote access. The exploitation activity is within the local network.
46. Which Cisco appliance can be used to filter network traffic contents to report and deny traffic based on the web server reputation?
- WSA
- AVC
- ASA
- ESA
Explanation: The Cisco Web Security Appliance (WSA) acts as a web proxy for an enterprise network. WSA can provide many types of logs related to web traffic security including ACL decision logs, malware scan logs, and web reputation filtering logs. The Cisco Email Security Appliance (ESA) is a tool to monitor most aspects of email delivery, system functioning, antivirus, antispam operations, and blacklist and whitelist decisions. The Cisco ASA is a firewall appliance. The Cisco Application Visibility and Control (AVC) system combines multiple technologies to recognize, analyze, and control over 1000 applications.
47. Which evasion method describes the situation that after gaining access to the administrator password on a compromised host, a threat actor is attempting to login to another host using the same credentials?
- pivoting
- traffic substitution
- resource exhaustion
- protocol-level misinterpretation
Explanation: Pivoting is an evasion method that assumes the threat actor has compromised an inside host and the actor wants to expand the access further into the compromised network.
48. What are two examples of DoS attacks? (Choose two.)
- port scanning
- SQL injection
- ping of death
- phishing
- buffer overflow
Explanation: The buffer overflow and ping of death DoS attacks exploit system memory-related flaws on a server by sending an unexpected amount of data or malformed data to the server.
49. Which type of attack is carried out by threat actors against a network to determine which IP addresses, protocols, and ports are allowed by ACLs?
- social engineering
- denial of service
- phishing
- reconnaissance
Explanation: Packet filtering ACLs use rules to filter incoming and outgoing traffic. These rules are defined by specifying IP addresses, port numbers, and protocols to be matched. Threat actors can use a reconnaissance attack involving port scanning or penetration testing to determine which IP addresses, protocols, and ports are allowed by ACLs.
50. Refer to the exhibit. A security analyst is reviewing an alert message generated by Snort. What does the number 2100498 in the message indicate?

- the id of the user that triggers the alert
- the message length in bits
- the Snort rule that is triggered
- the session number of the message
Explanation: The sid field in a Snort alert message indicates the Snort security rule that is triggered.
51. Which two attacks target web servers through exploiting possible vulnerabilities of input functions used by an application? (Choose two.)
- SQL injection
- port scanning
- port redirection
- trust exploitation
- cross-site scripting
Explanation: When a web application uses input fields to collect data from clients, threat actors may exploit possible vulnerabilities for entering malicious commands. The malicious commands that are executed through the web application might affect the OS on the web server. SQL injection and cross-site scripting are two different types of command injection attacks.
52. Which security function is provided by encryption algorithms?
- key management
- authorization
- integrity
- confidentiality
Explanation: Encryption algorithms are used to provide data confidentiality, which ensures that if data is intercepted in transit, it cannot be read.
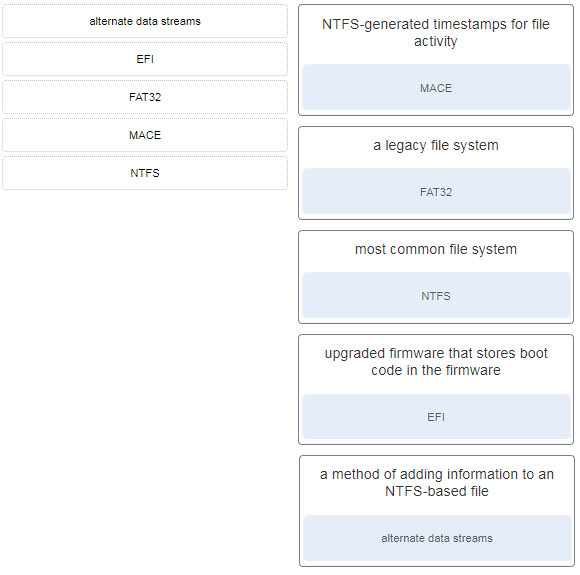
53. Match the Windows term to the description.
54. Which security endpoint setting would be used by a security analyst to determine if a computer has been configured to prevent a particular application from running?
- baselining
- blacklisting
- services
- whitelisting
Explanation: Blacklisting can be used on a local system or updated on security devices such as a firewall. Blacklists can be manually entered or obtained from a centralized security system. Blacklists are applications that are prevented from executing because they pose a security risk to the individual system and potentially the company.
55. Refer to the exhibit. Which technology would contain information similar to the data shown for infrastructure devices within a company?
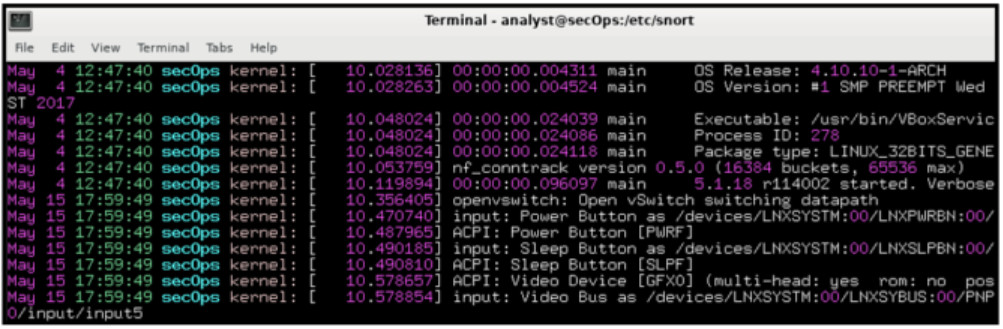
- Apache server
- firewall
- HIDS
- syslog server
Explanation: A syslog server consolidates and maintains messages from infrastructure devices that have been configured to send logging information. Data from the syslog server can be analyzed to detect anomalies.
56. At the request of investors, a company is proceeding with cyber attribution with a particular attack that was conducted from an external source. Which security term is used to describe the person or device responsible for the attack?
- threat actor
- fragmenter
- tunneler
- skeleton
Explanation: Some people may use the common word of “hacker” to describe a threat actor. A threat actor is an entity that is involved with an incident that impacts or has the potential to impact an organization in such a way that it is considered a security risk or threat.
57. Which Windows application is commonly used by a cybersecurity analyst to view Microsoft IIS access logs?
- Event Viewer
- Notepad
- SIEM
- Word
Explanation: Event Viewer is an application on a Windows-based device used to view event logs including IIS access logs.
58. Which two algorithms use a hashing function to ensure message integrity? (Choose two.)
- SEAL
- AES
- 3DES
- MD5
- SHA
Explanation: Hashing algorithms are used to provide data integrity, which ensures that the data has not changed during transmission. MD5 and SHA are commonly used hashing algorithms.
59. Which type of evidence cannot prove an IT security fact on its own?
- best
- corroborative
- indirect
- hearsay
Explanation: Indirect evidence cannot prove a fact on its own, but direct evidence can. Corroborative evidence is supporting information. Best evidence is most reliable because it is something concrete such as a signed contract.
60. Refer to the exhibit. Approximately what percentage of the physical memory is still available on this Windows system?
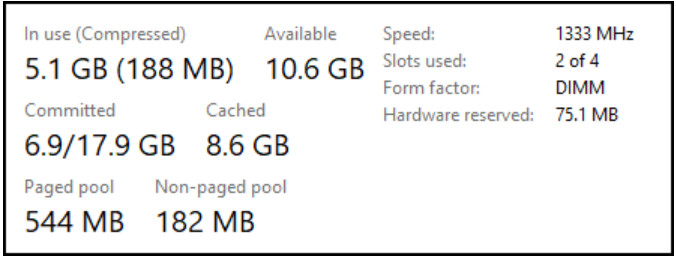
- 32%
- 53%
- 68%
- 90%
Explanation: The graphic shows that there is 5.1 GB (187 MB) of memory in use with 10.6 GB still available. Together this adds up to 16 GB of total physical memory. 5 GB is approximately 32% of 16 GB leaving 68% still available.
61. Which Windows tool can be used by a cybersecurity administrator to secure stand-alone computers that are not part of an active directory domain?
- PowerShell
- Windows Defender
- Local Security Policy
- Windows Firewall
Explanation: Windows systems that are not part of an Active Directory Domain can use the Windows Local Security Policy to enforce security settings on each stand-alone system.
62. What are three benefits of using symbolic links over hard links in Linux? (Choose three.)
- They can show the location of the original file.
- Symbolic links can be exported.
- They can be compressed.
- They can be encrypted.
- They can link to a directory.
- They can link to a file in a different file system.
Explanation: In Linux, a hard link is another file that points to the same location as the original file. A soft link (also called a symbolic link or a symlink) is a link to another file system name. Hard links are limited to the file system in which they are created and they cannot link to a directory; soft links are not limited to the same file system and they can link to a directory. To see the location of the original file for a symbolic link use the ls –l command.
63. When attempting to improve system performance for Linux computers with a limited amount of memory, why is increasing the size of the swap file system not considered the best solution?
- A swap file system uses hard disk space to store inactive RAM content.
- A swap file system cannot be mounted on an MBR partition.
- A swap file system only supports the ex2 file system.
- A swap file system does not have a specific file system.
Explanation: The swap file system is used by Linux when it runs out of physical memory. When needed, the kernel moves inactive RAM content to the swap partition on the hard disk. Storing and retrieving content in the swap partition is much slower than RAM is, and therefore using the swap partition should not be considered the best solution to improving system performance.
64. Refer to the exhibit. A security analyst is reviewing the logs of an Apache web server. Which action should the analyst take based on the output shown?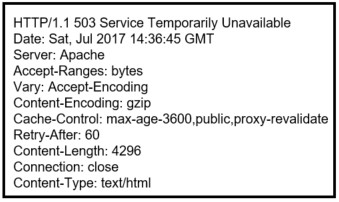
- Notify the appropriate security administration for the country.
- Restart the server.
- Notify the server administrator.
- Ignore the message.
Explanation: An Apache web server is an open source server that delivers web pages. Security access logs for an Apache web server include a 3-digit HTTP code that represents the status of the web request. A code that begins with 2 indicates access success. A code that begins with 3 represents redirection. A code that begins with 4 represents a client error and a code that begins with 5 represents a server error. The server administrator should be alerted if a server error such as the 503 code occurs.
65. A security professional is making recommendations to a company for enhancing endpoint security. Which security endpoint technology would be recommended as an agent-based system to protect hosts against malware?
- IPS
- HIDS
- baselining
- blacklisting
Explanation: A host-based intrusion detection systems (HIDS) is a comprehensive security application that provides antimalware applications, a firewall, and monitoring and reporting.
66. Which technique could be used by security personnel to analyze a suspicious file in a safe environment?
- whitelisting
- baselining
- sandboxing
- blacklisting
Explanation: Sandboxing allows suspicious files to be executed and analyzed in a safe environment. There are free public sandboxes that allow for malware samples to be uploaded or submitted and analyzed.
67. A cybersecurity analyst has been called to a crime scene that contains several technology items including a computer. Which technique will be used so that the information found on the computer can be used in court?
- rootkit
- log collection
- Tor
- unaltered disk image
Explanation: A normal file copy does not recover all data on a storage device so an unaltered disk image is commonly made. An unaltered disk image preserves the original evidence, thus preventing inadvertent alteration during the discovery phase. It also allows recreation of the original evidence.
68. Which SOC technology automates security responses by using predefined playbooks which require a minimum amount of human intervention?
- SOAR
- Wireshark
- NetFlow
- SIEM
- syslog
Explanation: SOAR technology goes a step further than SIEM by integrating threat intelligence and automating incident investigation and response workflows based on playbooks developed by the security team.
69. What is the first line of defense when an organization is using a defense-in-depth approach to network security?
- proxy server
- firewall
- IPS
- edge router
Explanation: A defense-in-depth approach uses layers of security measures starting at the network edge, working through the network, and finally ending at the network endpoints. Routers at the network edge are the first line of defense and forward traffic intended for the internal network to the firewall.
70. Which access control model assigns security privileges based on the position, responsibilities, or job classification of an individual or group within an organization?
- rule-based
- role-based
- discretionary
- mandatory
Explanation: Role-based access control models assign privileges based on position, responsibilities, or job classification. Users and groups with the same responsibilities or job classification share the same assigned privileges. This type of access control is also referred to as nondiscretionary access control.
71. Which metric in the CVSS Base Metric Group is used with an attack vector?
- the presence or absence of the requirement for user interaction in order for an exploit to be successful
- the number of components, software, hardware, or networks, that are beyond the control of the attacker and that must be present in order for a vulnerability to be successfully exploited
- the determination whether the initial authority changes to a second authority during the exploit
- the proximity of the threat actor to the vulnerability
Explanation: The attack vector is one of several metrics defined in the Common Vulnerability Scoring System (CVSS) Base Metric Group Exploitability metrics. The attack vector is how close the threat actor is to the vulnerable component. The farther away the threat actor is to the component, the higher the severity because threat actors close to the network are easier to detect and mitigate.
72. Which field in the IPv6 header points to optional network layer information that is carried in the IPv6 packet?
- traffic class
- flow label
- next header
- version
Explanation: Optional Layer 3 information about fragmentation, security, and mobility is carried inside of extension headers in an IPv6 packet. The next header field of the IPv6 header acts as a pointer to these optional extension headers if they are present.
73. Which data security component is provided by hashing algorithms?
- integrity
- confidentiality
- key exchange
- authentication
Explanation: Hashing algorithms are used to provide message integrity, which ensures that data in transit has not changed or been altered.
74. Which attack surface, defined by the SANS Institute, is delivered through the exploitation of vulnerabilities in web, cloud, or host-based applications?
- human
- network
- host
- software
Explanation: The SANS Institute describes three components of the attack surface:
- Network Attack Surface – exploits vulnerabilities in networks
- Software Attack Surface – delivered through the exploitation of vulnerabilities in web, cloud, or host-based software applications
- Human Attack Surface – exploits weaknesses in user behavior
75. What is the main goal of using different evasion techniques by threat actors?
- to launch DDoS attacks on targets
- to identify vulnerabilities of target systems
- to prevent detection by network and host defenses
- to gain the trust of a corporate employee in an effort to obtain credentials
Explanation: Many threat actors use stealthy evasion techniques to disguise an attack payload because the malware and attack methods are most effective if they are undetected. The goal is to prevent detection by network and host defenses.
76. How can NAT/PAT complicate network security monitoring if NetFlow is being used?
- It disguises the application initiated by a user by manipulating port numbers.
- It changes the source and destination MAC addresses.
- It conceals the contents of a packet by encrypting the data payload.
- It hides internal IP addresses by allowing them to share one or a few outside IP addresses.
Explanation: NAT/PAT maps multiple internal IP addresses with only a single or a few outside IP addresses breaking end-to-end flows. The result makes it difficult to log the inside device that is requesting and receiving the traffic. This is especially a problem with a NetFlow application because NetFlow flows are unidirectional and are defined by the addresses and ports that they share.
77. Which statement describes the function provided by the Tor network?
- It conceals packet contents by establishing end-to-end tunnels.
- It distributes user packets through load balancing.
- It allows users to browse the Internet anonymously.
- It manipulates packets by mapping IP addresses between two networks.
Explanation: Tor is a software platform and network of P2P hosts that function as Internet routers on the Tor network. The Tor network allows users to browse the Internet anonymously.
78. When establishing a server profile for an organization, which element describes the type of service that an application is allowed to run on the server?
- user account
- listening port
- service account
- software environment
Explanation: A server profile should contain some important elements including these:
- Listening ports – the TCP and UDP daemons and ports that are allowed to be open on the server
- User accounts – the parameters defining user access and behavior
- Service accounts – the definitions of the type of service that an application is allowed to run on a server
- Software environment – the tasks, processes, and applications that are permitted to run on the server
79. What will a threat actor do to create a back door on a compromised target according to the Cyber Kill Chain model?
- Add services and autorun keys.
- Collect and exfiltrate data.
- Open a two-way communications channel to the CnC infrastructure.
- Obtain an automated tool to deliver the malware payload.
Explanation: Once a target system is compromised, the threat actor will establish a back door into the system to allow for continued access to the target. Adding services and autorun keys is a way to create a point of persistent access.
80. Which three things will a threat actor do to prepare a DDoS attack against a target system on the Internet? (Choose three.)
- Install a black door on the target system.
- Obtain an automated tool to deliver the malware payload.
- Establish two-way communications channels to the CnC infrastructure with zombies.
- Collect and exfiltrate data.
- Compromise many hosts on the Internet.
- Install attack software on zombies.
Explanation: To prepare for launching a DDoS attack, a threat actor will compromise many hosts on the Internet, called zombies. The threat actor will then install attack software on zombies and establish a two-way communications channel to CnC infrastructure with zombies. The threat actor will issue the command to zombies through the CnC to launch a DDoS attack against a target system.
81. What is specified in the plan element of the NIST incident response plan?
- organizational structure and the definition of roles, responsibilities, and levels of authority
- metrics for measuring the incident response capability and effectiveness
- priority and severity ratings of incidents
- incident handling based on the mission of the organization
Explanation: NIST recommends creating policies, plans, and procedures for establishing and maintaining a CSIRC. One component of the plan element is to develop metrics for measuring the incident response capability and its effectiveness.
82. What is the responsibility of the IT support group when handing an incident as defined by NIST?
- coordinates the incident response with other stakeholders and minimizes the damage of an incident
- performs disciplinary measures if an incident is caused by an employee
- performs actions to minimize the effectiveness of the attack and preserve evidence
- reviews the incident policies, plans, and procedures for local or federal guideline violations
Explanation: IT support best understands the technology used in the organization and can perform the correct actions to minimize the effectiveness of the attack and preserve evidence.
83. What is an example of privilege escalation attack?
- A DDoS attack is launched against a government server and causes the server to crash.
- A port scanning attack finds that the FTP service is running on a server that allows anonymous access.
- A threat actor performs an access attack and gains the administrator password.
- A threat actor sends an email to an IT manager to request the root access.
Explanation: With the privilege escalation exploit, vulnerabilities in servers or access control systems are exploited to grant an unauthorized user, or software process, higher levels of privilege than either should have. After the higher privilege is granted, the threat actor can access sensitive information or take control of a system.
84. A threat hunter is concerned about a significant increase in TCP traffic sourced from port 53. It is suspected that malicious file transfer traffic is being tunneled out using the TCP DNS port. Which deep packet inspection tool can detect the type of application originating the suspicious traffic?
- syslog analyzer
- NBAR2
- NetFlow
- IDS/IPS
- Wireshark
Explanation: NBAR2 is used to discover the applications that are responsible for network traffic. NBAR is a classification engine that can recognize a wide variety of applications, including web-based applications and client/server applications.
85. Which type of evaluation includes the assessment of the likelihood of an attack, the type of threat actor likely to perpetrate such an attack, and what the consequences could be to the organization if the exploit is successful?
- penetration testing
- risk analysis
- vulnerability identification
- server profiling
86. When establishing a network profile for an organization, which element describes the time between the establishment of a data flow and its termination?
- session duration
- total throughput
- routing protocol convergence
- bandwidth of the Internet connection
Explanation: A network profile should include some important elements, such as the following:
- Total throughput – the amount of data passing from a given source to a given destination in a given period of time
- Session duration – the time between the establishment of a data flow and its termination
- Ports used – a list of TCP or UDP processes that are available to accept data
- Critical asset address space – the IP addresses or the logical location of essential systems or data
87. Which term describes a threat actor who has advanced skills and pursues a social agenda?
- organized crime
- script kiddie
- corporate/industrial spies
- hacktivist
Explanation: Threat actors who have advanced hacking abilities and pursue a social or political agenda are known as hacktivists.
88. Refer to the exhibit. A security specialist is checking if files in the directory contain ADS data. Which switch should be used to show that a file has ADS attached?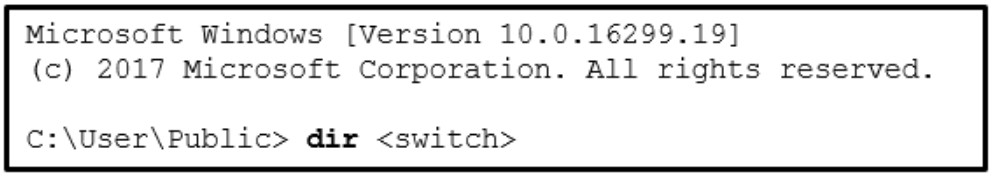
- /a
- /r
- /d
- /s
Explanation: By using NTFS, Alternate Data Streams (ADSs) can be connected to a file as an attribute called $DATA. The command dir /r can be used to see if a file contains ADS data.
89. The SOC manager is reviewing the metrics for the previous calendar quarter and discovers that the MTTD for a breach of password security perpetrated through the Internet was forty days. What does the MTTD metric represent within the SOC?
- window of time required to stop the spread of malware in the network
- the average time that it takes to identify valid security incidents that have occurred
- the time required to stop the incident from causing further damage to systems or data
- the average time that it takes to stop and remediate a security incident
Explanation: Cisco defines MTTD as the average time that it takes for the SOC personnel to identify that valid security incidents have occurred in the network.
90. A cybersecurity analyst is performing a CVSS assessment on an attack where a web link was sent to several employees. Once clicked, an internal attack was launched. Which CVSS Base Metric Group Exploitability metric is used to document that the user had to click on the link in order for the attack to occur?
- scope
- integrity requirement
- availability requirement
- user interaction
Explanation: The CVSS Base Metric Group has the following metrics: attack vector, attack complexity, privileges required, user interaction, and scope. The user interaction metric expresses the presence or absence of the requirement for user interaction in order for an exploit to be successful.
91. When a server profile for an organization is being established, which element describes the TCP and UDP daemons and ports that are allowed to be open on the server?
- critical asset address space
- service accounts
- software environment
- listening ports
Explanation: A server profile will often contain the following:
- Listening ports – the TCP and UDP daemons and ports that are allowed to be open on the server
- User accounts – the parameters defining user access and behavior
- Service accounts – the definitions of the type of service that an application is allowed to run on a server
- Software environment – the tasks, processes, and applications that are permitted to run on the server
92. Which two actions should be taken during the preparation phase of the incident response life cycle defined by NIST? (Choose two.)
- Fully analyze the incident.
- Meet with all involved parties to discuss the incident that took place.
- Detect all the incidents that occurred.
- Acquire and deploy the tools that are needed to investigate incidents.
- Create and train the CSIRT
Explanation: According to the guideline defined in the NIST Incident Response Life Cycle, several actions should be taken during the preparation phase including (1) creating and training the CSIRT and (2) acquiring and deploying the tools needed by the team to investigate incidents.
93. Match the NIST incident response stakeholder with the role.
94. Match the file system term used in Linux to the function.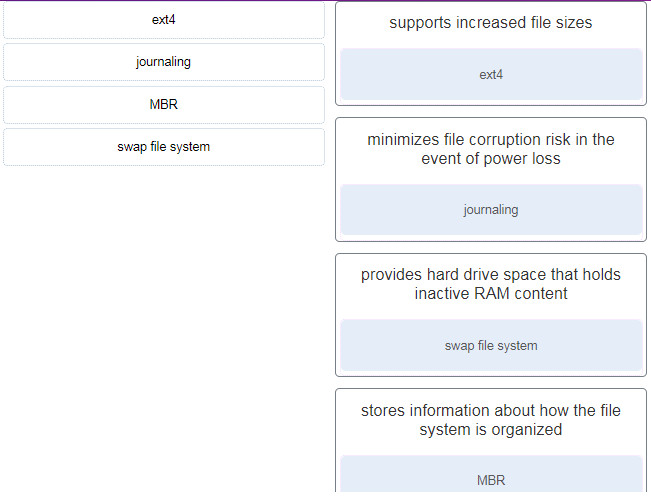
- supports increased file sizes –> ext4
- minimizes file corruption risk in the event of power loss –> journaling
- provides hard drive space that holds inactive RAM content –> swap file system
- stores information about how the file system is organized –> MBR
95. Which information security component is compromised in a DDoS attack?
- accountability
- confidentiality
- integrity
- availability
Explanation: Confidentiality, integrity, and availability are the elements contained in the CIA triad. Availability means that all authorized users have uninterrupted access to important resources and data. In a DDoS attack, servers and services are overloaded and applications are no longer available to users.