Lab Objective:
The objective of this lab exercise is to ensure that learned MAC addresses on a secured port are retained in the switch’s NVRAM in the event of a reboot. By default, secured MAC addresses are flushed during switch reboots.
Lab Purpose:
Retaining learned secure MAC addresses is an advanced skill. When a Cisco Catalyst Switch configured with port security reboots, learned secure MAC address entries are flushed and have to be relearned when the switch comes back up. As a Cisco engineer, understanding advanced features will give you the edge over your fellow CCNAs.
Certification Level:
This lab is suitable for CCENT and CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 6/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 15 minutes.
Lab Topology:
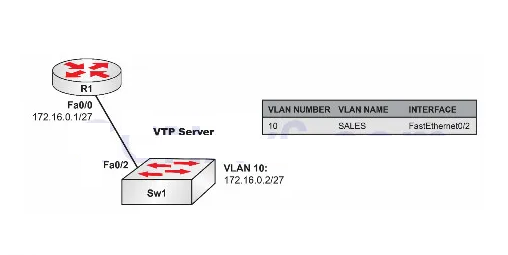
Please use the following topology to complete this lab exercise:

Task 1:
Configure hostnames on Sw1 and R1 as illustrated in the topology.
Task 2:
Create VLAN10 on Sw1 and assign port FastEthernet0/2 to this VLAN as an access port.
Task 3:
Configure IP address 172.16.0.1/27 on R1’s FastEthernet0/0 interface and IP address 172.16.0.2/27 on Sw2’s VLAN10 interface. Verify that R1 can ping Sw1, and vice versa. Task 4: Configure port security on port FastEthernet0/2 on Sw1 so that any MAC addresses learned on that interface are written to the switch’s NVRAM. The NVRAM is the startup configuration. Verify your configuration with port-security commands in Cisco IOS.
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
For reference information on configuring and verifying VLANs, please refer to earlier labs.
Task 3:
For reference information on configuring and verifying IP addresses, please refer to earlier labs.
Task 4:
Sw1#conf t
Enter configuration commands, one per line. End with CTRL/Z.
Sw1(config)#interface fastethernet0/2
Sw1(config-if)#switchport port-security
Sw1(config-if)#switchport port-security mac-address sticky
Sw1(config-if)#end
Sw1#
Sw1#copy startup-config running-config
Destination filename [running-config]?
2167 bytes copied in 2.092 secs (1036 bytes/sec)
Sw1#
Sw1#show port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Sec Action
(Count) (Count) (Count)
----------------------------------------------------------------------
Fa0/2 1 1 0 Shutdown
----------------------------------------------------------------------
Total Addresses in System : 1
Max Addresses limit in System : 1024
Sw1#show running-config interface fastethernet0/2
Building configuration...
Current configuration : 254 bytes
!
interface FastEthernet0/2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 0004.c058.5fc0
endNOTE: When configuring port security, by default the learned MAC addresses are flushed when the switch is reloaded. To prevent this and ensure that the switch preserves MAC addresses that are dynamically learned via port security, you need to configure sticky learning. This configuration, in conjunction with the copy run start command, saves the learned MAC addresses to NVRAM. This means that when the switch is rebooted, the MAC addresses learned are not lost. The switch adds the switchport port-security mac-address sticky <mac-address> command dynamically under the interface for every sticky dynamically learned MAC address. So if 100 MAC addresses are learned this way, the switch would add 100 of these statements after the switchport port-security mac-address sticky command that you issued under the interface. Be very careful because this can create a very large configuration file in the real world!