| How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank. |
|
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
|
SRWE Final Skills Exam (Equipment)
Your exam may be different
Topology
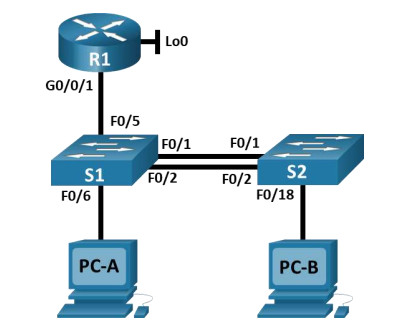
CCNAv7 SRWE Skills Assessment
Assessment Objectives
- Part 1: Initialize, Reload and Configure Basic Device Settings (45 points, 45 minutes)
- Part 2: Configure Network Infrastructure Settings (VLANs, Trunking, Etherchannel) (30 points, 25 minutes)
- Part 3: Configure Host Support (20 points, 25 minutes)
- Part 4: Test and Verify IPv4 and IPv6 End-to-End Connectivity (5 points, 10 minutes)
Scenario
In this Skills Assessment (SA) you will configure the devices in a small network. You must configure a router, switch and PCs to support both IPv4 and IPv6 connectivity for supported hosts. Your router and switch must also be managed securely. You will configure inter-VLAN routing, DHCP, Etherchannel, and port-security.
Required Resources
- 1 Router (Cisco 4221 with Cisco IOS XE Release 16.9.4 universal image or comparable)
- 2 Switches (Cisco 2960 with Cisco IOS Release 15.2(2) lanbasek9 image or comparable)
- 2 PCs (Windows with a terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
VLAN Table
Addressing Table
| VLAN | VLAN Name |
|---|---|
| 2 | Bikes |
| 3 | Trikes |
| 4 | Management |
| 5 | Parking |
| 6 | Native |
Addressing Table
| Device / Interface | IP Address / Prefix | Default Gateway |
|---|---|---|
| R1 G0/0/1.2 | 10.19.8.1 /26 | N/A |
| 2001:db8:acad:a::1 /64 | N/A | |
| R1 G0/0/1.3 | 10.19.8.65 /27 | N/A |
| 2001:db8:acad:b::1 /64 | N/A | |
| R1 G0/0/1.4 | 10.19.8.97 /29 | N/A |
| 2001:db8:acad:c::1 /64 | N/A | |
| R1 G0/0/1.6 | N/A | N/A |
| R1 Loopback0 | 209.165.201.1 /27 | N/A |
| 2001:db8:acad:209::1 /64 | N/A | |
| S1 VLAN 4 | 10.19.8.98 /29 | 10.19.8.97 |
| 2001:db8:acad:c::98 /64 | N/A | |
| fe80::98 | N/A | |
| S2 VLAN 4 | 10.19.8.99 /29 | 10.19.8.97 |
| 2001:db8:acad:c::99 /64 | N/A | |
| fe80::99 | N/A | |
| PC-A NIC | DHCP for IPv4 address | DHCP for IPv4 default gateway |
| 2001:db8:acad:a::50 /64 | fe80::1 | |
| PC-B NIC | DHCP for IPv4 address | DHCP for IPv4 default gateway |
| 2001:db8:acad:b::50 /64 | fe80::1 |
Note: There is no interface on the router supporting VLAN 5.
Instructions
Part 1: Initialize, Reload and Configure Basic Device Settings
- Total points: 45
- Time: 20 minutes
Step 1: Initialize and reload router and switch.
- Erase the startup configurations and VLANs from the router and switch and reload the devices.
- After the switch is reloaded, configure the SDM template to support IPv6 as needed, and reload the switch again.
- Before proceeding, have your instructor verify device initializations.
Use the console cable to connect from PC-A to the Router/Switch (console port)
Go to PC-A, Desktop tab, Terminal app
Router, Switch1, Switch 2:
Router/Switchs >enable Router/Switchs #erase startup-config Erasing the nvram filesystem will remove all configuration files! Continue? [confirm] [OK] Erase of nvram: complete %SYS-7-NV_BLOCK_INIT: Initialized the geometry of nvram Router/Switchs #reload System configuration has been modified. Save? [yes/no]:yes Building configuration... [OK]
Switch1 & Switch 2:
Switch(config)# sdm prefer dual-ipv4-and-ipv6 default
Switch(config)# exit
Switch# reload
Proceed with reload? [confirm]Step 2: Configure R1.
Configuration tasks for R1 include the following:
| Task | Specification | Points |
|---|---|---|
| Disable DNS lookup | 0.5 pt | |
| Router name | R1 | 0.5 pt |
| Domain name | ccna-lab.com | 0.5 pt |
| Encrypted privileged EXEC password | ciscoenpass | 1 pt |
| Console access password | ciscoconpass | 1 pt |
| Set the minimum length for passwords | 10 characters | 1 pt |
| Create an administrative user in the local database | Username: admin Password: admin1pass | 1 pt |
| Set login on VTY lines to use local database | 1 pt | |
| Set VTY lines to accept SSH connections only | 1 pt | |
| Encrypt the clear text passwords | 1 pt | |
| Configure an MOTD Banner | 0.5 pt | |
| Enable IPv6 Routing | 1 pt | |
| Configure Interface G0/0/1 and sub interfaces | Set the description Set the IPv4 address Set the IPv6 Link Local Address as fe80::1 Set the IPv6 address Activate Interface | 4 pts |
| Configure the Loopback0 interface | Set the description Set the IPv4 address Set the IPv6 address Set the IPv6 Link Local Address as fe80::1 | 2 pts |
| Generate an RSA crypto key | 1024 bits modulus | 1 pt |
Router>enable
Router#config terminal
Router(config)#no ip domain lookup
Router(config)#hostname R1
R1(config)#ip domain name ccna-lab.com
R1(config)#enable secret ciscoenpass
R1(config)#line console 0
R1(config-line)#password ciscoconpass
R1(config-line)#login
R1(config-line)#exit
R1(config)#security passwords min-length 10
R1(config)#username admin secret admin1pass
R1(config)#line vty 0 15
R1(config-line)#login local
R1(config-line)#transport input ssh
R1(config-line)#exit
R1(config)#service password-encryption
R1(config)#banner motd #Unauthorized Acess is Prohibited#
R1(config)#ipv6 unicast-routing
R1(config)#interface g0/0/1.2
R1(config-subif)#encapsulation dot1Q 2
R1(config-subif)#description Bikes
R1(config-subif)#ip address 10.19.8.1 255.255.255.192
R1(config-subif)#ipv6 address 2001:db8:acad:a::1/64
R1(config-subif)#ipv6 address fe80::1 link-local
R1(config-subif)#interface g0/0/1.3
R1(config-subif)#encapsulation dot1Q 3
R1(config-subif)#description Trikes
R1(config-subif)#ip address 10.19.8.65 255.255.255.224
R1(config-subif)#ipv6 address 2001:db8:acad:b::1/64
R1(config-subif)#ipv6 address fe80::1 link-local
R1(config-subif)#interface g0/0/1.4
R1(config-subif)#encapsulation dot1Q 4
R1(config-subif)#description Management
R1(config-subif)#ip address 10.19.8.97 255.255.255.248
R1(config-subif)#ipv6 address 2001:db8:acad:c::1/64
R1(config-subif)#ipv6 address fe80::1 link-local
R1(config-subif)#interface g0/0/1.6
R1(config-subif)#encapsulation dot1Q 6
R1(config-subif)#description Native
R1(config)#interface g0/0/1
R1(config-if)#no shutdown
R1(config-subif)#interface Loopback 0
R1(config-subif)#description Loopback
R1(config-subif)#ip address 209.165.201.1 255.255.255.224
R1(config-subif)#ipv6 address 2001:db8:acad:209::1/64
R1(config-subif)#ipv6 address fe80::1 link-local
R1(config-subif)#description Native
R1(config-subif)#exit
R1(config)#crypto key generate rsa
1024Step 3: Configure S1 and S2.
Configuration tasks for the switches include the following:
| Task | Specification | S1 | S2 |
|---|---|---|---|
| Disable DNS lookup | 0.5pt | 0.5pt | |
| Switch name | S1 or S2, as appropriate | 0.5pt | 0.5pt |
| Domain name | ccna-lab.com | 0.5pt | 0.5pt |
| Encrypted privileged EXEC password | ciscoenpass | 1pt | 1pt |
| Console access password | ciscoconpass | 1pt | 1pt |
| Create an administrative user in the local database | Username: admin Password: admin1pass | 1pt | 1pt |
| Set login on VTY lines to use local database | 1pt | 1pt | |
| Set VTY lines to accept SSH connections only | 1pt | 1pt | |
| Encrypt the clear text passwords | 1pt | 1pt | |
| Configure an MOTD Banner | 0.5pt | 0.5pt | |
| Generate an RSA crypto key | 1024 bits modulus | 1pt | 1pt |
| Configure Management Interface (SVI) | Set the Layer 3 IPv4 address Set the Ipv6 Link Local Address as FE80::98 for S1 and FE80::99 for S2 Set the Layer 3 IPv6 address | 2pts | 2pts |
| Configure Default Gateway | Configure the default gateway as 10.19.8.97 for IPv4 | 1pt | 1pt |
Switch1>enable
Switch1#conf t
Switch1(config)#no ip domain lookup
Switch1(config)#hostname S1
S1(config)#ip domain name ccna-lab.com
S1(config)#enable secret ciscoenpass
S1(config)#line console 0
S1(config-line)#password ciscoconpass
S1(config-line)#login
S1(config-line)#exit
S1(config)#username admin secret admin1pass
S1(config)#line vty 0 15
S1(config-line)#login local
S1(config-line)#transport input ssh
S1(config-line)#exit
S1(config)#service password-encryption
S1(config)#banner motd #Unauthorized Access is Prohibitted!#
S1(config)#crypto key generate rsa
1024
S1(config)#interface vlan 4
S1(config-if)#ip address 10.19.8.98 255.255.255.248
S1(config-if)#ipv6 address 2001:db8:acad:c::98/64
S1(config-if)#ipv6 address fe80::98 link-local
S1(config-if)#description Management Interface
S1(config-if)#no shutdown
S1(config-if)#exit
S1(config)#ip default-gateway 10.19.8.97Switch2>enable
Switch2#conf t
Switch2(config)#no ip domain lookup
Switch2(config)#hostname S2
S2(config)#ip domain name ccna-lab.com
S2(config)#enable secret ciscoenpass
S2(config)#line console 0
S2(config-line)#password ciscoconpass
S2(config-line)#login
S2(config-line)#exit
S2(config)#username admin secret admin1pass
S2(config)#line vty 0 15
S2(config-line)#login local
S2(config-line)#transport input ssh
S2(config-line)#exit
S2(config)#service password-encryption
S2(config)#banner motd #Unauthorized Access is Prohibitted!#
S2(config)#crypto key generate rsa
1024
S2(config)#interface vlan 4
S2(config-if)#ip address 10.19.8.99 255.255.255.248
S2(config-if)#ipv6 address 2001:db8:acad:c::99/64
S2(config-if)#ipv6 address fe80::99 link-local
S2(config-if)#description Management Interface
S2(config-if)#no shutdown
S2(config-if)#exit
S2(config)#ip default-gateway 10.19.8.97Points for Step 1 (4 points):
Points for Step 2 (17 points):
Points for Step 3 (24 points):
Instructor Sign-off Part 1:
Instructor Sign-off
Total Points for Part 1 (45 points)
Part 2: Configure Network Infrastructure Settings (VLANs, Trunking, EtherChannel)
- Total points: 30
- Time: 20 minutes
Step 1: Configure S1.
Configuration tasks for S1 include the following:
| Task | Specification | Points |
|---|---|---|
| Create VLANs | VLAN 2, name Bikes VLAN 3, name Trikes VLAN 4, name Management VLAN 5, name Parking VLAN 6, name Native | 5 points |
| Create 802.1Q trunks that use the native VLAN 6 | Interfaces F0/1, F0/2, and F0/5 | 1 point |
| Create a Layer 2 EtherChannel port group that uses interfaces F0/1 and F0/2 | Use the LACP protocol for negotiation | 2 points |
| Configure host access port for VLAN 2 | Interface F0/6 | 1 point |
| Configure port-security on access ports | Allow 3 MAC addresses | 2 points |
| Secure all unused interfaces | Assign to VLAN 5, Set to access mode, add a description, and shutdown | 4 points |
S1(config)#vlan 2
S1(config-vlan)#name Bikes
S1(config-vlan)#vlan 3
S1(config-vlan)#name Trikes
S1(config-vlan)#vlan 4
S1(config-vlan)#name Management
S1(config-vlan)#vlan 5
S1(config-vlan)#name Parking
S1(config-vlan)#vlan 6
S1(config-vlan)#name Native
S1(config)#interface range f0/1-2
S1(config-if-range)#switchport trunk encapsulation dot1q (#option)
S1(config-if-range)#switchport mode trunk
S1(config-if-range)#switchport trunk native vlan 6
S1(config-if-range)#switchport trunk allowed vlan 2-6
S1(config-if-range)#exit
S1(config)#interface f0/5
S1(config-if)#switchport trunk encapsulation dot1q (#option)
S1(config-if)#switchport mode trunk
S1(config-if)#switchport trunk native vlan 6
S1(config-if)#switchport trunk allowed vlan 2-6
S1(config-if)#exit
S1(config)#interface range f0/1-2
S1(config-if-range)#channel-group 1 mode active
S1(config-if-range)#exit
S1(config)#interface f0/6
S1(config-if)#switchport mode access
S1(config-if)#switchport access vlan 2
S1(config-if)#switchport port-security maximum 3
S1(config)#interface range f0/3-4
S1(config-if-range)#switchport mode access
S1(config-if-range)#switchport access vlan 5
S1(config-if-range)#description Unused Interfaces
S1(config-if-range)#shutdown
S1(config)#interface range f0/7-24
S1(config-if-range)#switchport mode access
S1(config-if-range)#switchport access vlan 5
S1(config-if-range)#description Unused Interfaces
S1(config-if-range)#shutdown
S1(config)#interface range g0/1-2
S1(config-if-range)#switchport mode access
S1(config-if-range)#switchport access vlan 5
S1(config-if-range)#description Unused Interfaces
S1(config-if-range)#shutdown Note: This configuration assumes the use of Cisco Catalyst 2960 switches which automatically use 802.1Q encapsulation on trunk links. Other switches may require manual configuration of the encapsulation. Always configure both ends of a trunk link with the same native VLAN. If 802.1Q trunk configuration is not the same on both ends, Cisco IOS Software reports errors.
Step 2: Configure S2.
Configuration tasks for S2 include the following:
| Task | Specification | Points |
|---|---|---|
| Create VLANs | VLAN 2, name Bikes VLAN 3, name Trikes VLAN 4, name Management VLAN 5, name Parking VLAN 6, name Native | 5 points |
| Create 802.1Q trunks that use the native VLAN 6 | Interfaces F0/1 and F0/2 | 1 point |
| Create a Layer 2 EtherChannel port group that uses interfaces F0/1 and F0/2 | Use the LACP protocol for negotiation | 2 points |
| Configure host access port for VLAN 3 | Interface F0/18 | 1 point |
| Configure port-security on access ports | Allow 3 MAC addresses | 2 points |
| Secure all unused interfaces | Assign to VLAN 5, Set to access mode, add a description, and shutdown | 4 points |
S2(config)#vlan 2
S2(config-vlan)#name Bikes
S2(config-vlan)#vlan 3
S2(config-vlan)#name Trikes
S2(config-vlan)#vlan 4
S2(config-vlan)#name Management
S2(config-vlan)#vlan 5
S2(config-vlan)#name Parking
S2(config-vlan)#vlan 6
S2(config-vlan)#name Native
S2(config)#interface range f0/1-2
S2(config-if-range)#switchport trunk encapsulation dot1q (#option)
S2(config-if-range)#switchport mode trunk
S2(config-if-range)#switchport trunk native vlan 6
S2(config-if-range)#switchport trunk allowed vlan 2-6
S2(config-if-range)#exit
S2(config)#interface range f0/1-2
S2(config-if-range)#channel-group 1 mode active
S2(config-if-range)#exit
S2(config)#interface f0/18
S2(config-if)#switchport mode access
S2(config-if)#switchport access vlan 3
S2(config-if)#switchport port-security maximum 3
S2(config)#interface range f0/3-17
S2(config-if-range)#switchport mode access
S2(config-if-range)#switchport access vlan 5
S2(config-if-range)#description Unused Interfaces
S2(config-if-range)#shutdown
S2(config)#interface range f0/19-24
S2(config-if-range)#switchport mode access
S2(config-if-range)#switchport access vlan 5
S2(config-if-range)#description Unused Interfaces
S2(config-if-range)#shutdown
S2(config)#interface range g0/1-2
S2(config-if-range)#switchport mode access
S2(config-if-range)#switchport access vlan 5
S2(config-if-range)#description Unused Interfaces
S2(config-if-range)#shutdown Note: This configuration assumes the use of Cisco Catalyst 2960 switches which automatically use 802.1Q encapsulation on trunk links. Other switches may require manual configuration of the encapsulation. Always configure both ends of a trunk link with the same native VLAN. If 802.1Q trunk configuration is not the same on both ends, Cisco IOS Software reports errors.
Points for Step 1 (15 points):
Points for Step 2 (15 points):
Instructor Sign-off Part 2:
Instructor Sign-off
Total Points for Part 2 (30 points)
Part 3: Configure Host Support
- Total points: 20
- Time: 10 minutes
Step 1: Configure R1
Configuration Tasks for R1 include the following
| Task | Specification | Points |
|---|---|---|
| Configure Default Routing | Create a default routes for IPv4 and IPv6 that direct traffic to interface Loopback 0 | (4 points) |
| Configure IPv4 DHCP for VLAN 2 | Create a DHCP pool for VLAN 2, consisting of the last 10 addresses in the subnet only. Assign the domain name ccna-a.net and specify the default gateway address as the router interface address for the subnet involved | (6 points) |
| Configure IPv4 DHCP for VLAN 3 | Create a DHCP pool for VLAN 3, consisting of the last 10 addresses in the subnet only. Assign the domain name ccna-b.net and specify the default gateway address as the router interface address for the subnet involved | (6 points) |
R1(config)#ip route 0.0.0.0 0.0.0.0 loopback 0
R1(config)#ipv6 route ::/0 loopback 0
R1(config)#ip dhcp excluded-address 10.19.8.1 10.19.8.52
R1(config)#ip dhcp pool VLAN2-Bikes
R1(dhcp-config)#network 10.19.8.0 255.255.255.192
R1(dhcp-config)#default-router 10.19.8.1
R1(dhcp-config)#domain-name ccna-a.net
R1(dhcp-config)#exit
R1(config)#ip dhcp excluded-address 10.19.8.65 10.19.8.84
R1(config)#ip dhcp pool VLAN3-Trikes
R1(dhcp-config)#network 10.19.8.64 255.255.255.224
R1(dhcp-config)#default-router 10.19.8.65
R1(dhcp-config)#domain-name ccna-b.net
R1(dhcp-config)#Step 2: Configure host computers.
Configure the host computers PC-A and PC-B to use DHCP for IPv4 and statically assign the IPv6 GUA and
Link Local addresses. After configuring each host computer, record the host network settings with theipconfig /all command.
On PCs, go to Command Promt (cmd), Enter ipconfig /renew to request IP DMCP
| PC-A Network Configuration (2 points) | |
|---|---|
| Description | |
| Physical Address | |
| IP Address | |
| Subnet Mask | |
| Default Gateway | |
| IPv6 Default Gateway |
| PC-B Network Configuration (2 points) | |
|---|---|
| Description | |
| Physical Address | |
| IP Address | |
| Subnet Mask | |
| Default Gateway | |
| IPv6 Default Gateway |
Points for Step 1 (16 points):
Points for Step 2 (4 points):
Instructor Sign-off Part 3:
Instructor Sign-off
Total Points for Part 3 (20 points)
Part 4: Test and Verify End-to-End Connectivity
- Total points: 5
- Time: 10 minutes
Use the ping command to test IPv4 and IPv6 connectivity between all network devices.
Note: If pings to host computers fail, temporarily disable the computer firewall and retest.
Use the following table to methodically verify connectivity with each network device. Take corrective action to establish connectivity if a test fails:
| From | To | Protocol | IP Address | Ping Results |
|---|---|---|---|---|
| PC-A | R1, G0/0/1.2 R1, G0/0/1.2 | IPv4 | 10.19.8.1 | |
| IPv6 | 2001:db8:acad:a::1 | |||
| R1, G0/0/1.3 R1, G0/0/1.3 | IPv4 | 10.19.8.65 | ||
| IPv6 | 2001:db8:acad:b::1 | |||
| R1, G0/0/1.4 R1, G0/0/1.4 | IPv4 | 10.19.8.97 | ||
| IPv6 | 2001:db8:acad:c::1 | |||
| S1, VLAN 4 S1, VLAN 4 | IPv4 | 10.19.8.98 | ||
| IPv6 | 2001:db8:acad:c::98 | |||
| S2, VLAN 4 S2, VLAN 4 | IPv4 | 10.19.8.99. | ||
| IPv6 | 2001:db8:acad:c::99 | |||
| PC-B | IPv4 | IP address will vary. | ||
| IPv6 | 2001:db8:acad:b::50 | |||
| R1 Loop0 | IPv4 | 209.165.201.1 | ||
| IPv6 | 2001:db8:acad:209::1 | |||
| PC-B | R1 Loop0 | IPv4 | 209.165.201.1 | |
| IPv6 | 2001:db8:acad:209::1 | |||
| R1, G0/0/1.2 | IPv4 | 10.19.8.1 | ||
| IPv6 | 2001:db8:acad:a::1 | |||
| R1, G0/0/1.3 | IPv4 | 10.19.8.65 | ||
| IPv6 | 2001:db8:acad:b::1 | |||
| R1, G0/0/1.4 | IPv4 | 10.19.8.97 | ||
| IPv6 | 2001:db8:acad:c::1 | |||
| S1, VLAN 4 | IPv4 | 10.19.8.98 | ||
| IPv6 | 2001:db8:acad:c::98 | |||
| S2, VLAN 4 | IPv4 | 10.19.8.99. | ||
| IPv6 | 2001:db8:acad:c::99 |
Instructor Sign-off Part 4:
Instructor Sign-off
Total Points for Part 4 (5 points)
Enter score here.
Part 5: Cleanup
NOTE: DO NOT PROCEED WITH CLEANUP UNTIL YOUR INSTRUCTOR HAS GRADED YOUR SKILLS EXAM AND HAS INFORMED YOU THAT YOU MAY BEGIN CLEANUP.
Unless directed otherwise by the instructor, restore host computer network connectivity, and then turn off power to the host computers.
Before turning off power to the router and switch, remove the NVRAM configuration files (if saved) from both devices.
Disconnect and neatly put away all LAN cables that were used in the Final.
Router Interface Summary Table
| Router Model | Ethernet Interface #1 | Ethernet Interface #2 | Serial Interface #1 | Serial Interface #2 |
|---|---|---|---|---|
| 1800 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 1900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2801 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 2811 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 4221 | Gigabit Ethernet 0/0/0 (G0/0/0) | Gigabit Ethernet 0/0/1 (G0/0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 4300 | Gigabit Ethernet 0/0/0 (G0/0/0) | Gigabit Ethernet 0/0/1 (G0/0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many
interfaces the router has. There is no way to effectively list all the combinations of configurations for each router
class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device.
The table does not include any other type of interface, even though a specific router may contain one. An
example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be
used in Cisco IOS commands to represent the interface.