| How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank. |
|
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
|
CyberOps Associate (Version 1.0) – Modules 11 – 12: Network Infrastructure Security Group Exam
1. For which discovery mode will an AP generate the most traffic on a WLAN?
- passive mode
- mixed mode
- active mode
- open mode
2. Which parameter is commonly used to identify a wireless network name when a home wireless AP is being configured?
- ad hoc
- SSID
- BESS
- ESS
3. Which two protocols are considered distance vector routing protocols? (Choose two.)
- ISIS
- RIP
- BGP
- EIGRP
- OSPF
4. Which AAA component can be established using token cards?
- authentication
- accounting
- authorization
- auditing
5. Which statement describes a VPN?
- VPNs use open source virtualization software to create the tunnel through the Internet.
- VPNs use dedicated physical connections to transfer data between remote users.
- VPNs use logical connections to create public networks through the Internet.
- VPNs use virtual connections to create a private network through a public network.
6. What is an advantage of HIPS that is not provided by IDS?
- HIPS protects critical system resources and monitors operating system processes.
- HIPS deploys sensors at network entry points and protects critical network segments.
- HIPS monitors network processes and protects critical files.
- HIPS provides quick analysis of events through detailed logging.
7. Which statement describes a difference between RADIUS and TACACS+?
- RADIUS separates authentication and authorization whereas TACACS+ combines them as one process.
- RADIUS is supported by the Cisco Secure ACS software whereas TACACS+ is not.
- RADIUS uses TCP whereas TACACS+ uses UDP.
- RADIUS encrypts only the password whereas TACACS+ encrypts all communication.
8. What are two disadvantages of using an IDS? (Choose two.)
- The IDS does not stop malicious traffic.
- The IDS works offline using copies of network traffic.
- The IDS has no impact on traffic.
- The IDS analyzes actual forwarded packets.
- The IDS requires other devices to respond to attacks.
9. Which statement describes one of the rules that govern interface behavior in the context of implementing a zone-based policy firewall configuration?
- An administrator can assign interfaces to zones, regardless of whether the zone has been configured.
- An administrator can assign an interface to multiple security zones.
- By default, traffic is allowed to flow among interfaces that are members of the same zone.
- By default, traffic is allowed to flow between a zone member interface and any interface that is not a zone member.
10. Which technique is necessary to ensure a private transfer of data using a VPN?
- encryption
- virtualization
- scalability
- authorization
11. Which two devices would commonly be found at the access layer of the hierarchical enterprise LAN design model? (Choose two.)
- modular switch
- Layer 3 device
- Layer 2 switch
- firewall
- access point
12. Which two statements are true about NTP servers in an enterprise network? (Choose two.)
- There can only be one NTP server on an enterprise network.
- NTP servers at stratum 1 are directly connected to an authoritative time source.
- NTP servers control the mean time between failures (MTBF) for key network devices.
- NTP servers ensure an accurate time stamp on logging and debugging information.
- All NTP servers synchronize directly to a stratum 1 time source.
13. In the data gathering process, which type of device will listen for traffic, but only gather traffic statistics?
- NetFlow collector
- NMS
- SNMP agent
- syslog server
14. Which two protocols are link-state routing protocols? (Choose two.)
- ISIS
- EIGRP
- BGP
- RIP
- OSPF
15. What is the function of the distribution layer of the three-layer network design model?
- providing direct access to the network
- providing secure access to the Internet
- aggregating access layer connections
- providing high speed connection to the network edge
16. What two components of traditional web security appliances are examples of functions integrated into a Cisco Web Security Appliance? (Choose two.)
- email virus and spam filtering
- VPN connection
- firewall
- web reporting
- URL filtering
17. What are two types of addresses found on network end devices? (Choose two.)
- return
- IP
- MAC
- TCP
- UDP
18. What is a characteristic of the WLAN passive discover mode?
- The client must know the name of the SSID to begin the discover process.
- The client begins the discover process by sending a probe request.
- The beaconing feature on the AP is disabled.
- The AP periodically sends beacon frames containing the SSID.
19. What is a characteristic of a routed port that is configured on a Cisco switch?
- It supports subinterfaces.
- It is associated with a single VLAN.
- It runs STP to prevent loops.
- It is assigned an IP address.
20. What action does an Ethernet switch take when it receives a frame with an unknown Layer 2 source address?
- It forwards the frame out all interfaces except the interface on which it was received.
- It forwards the frame to the default gateway.
- It records the source address in the address table of the switch.
- It drops the frame.
21.. Match each device to a category.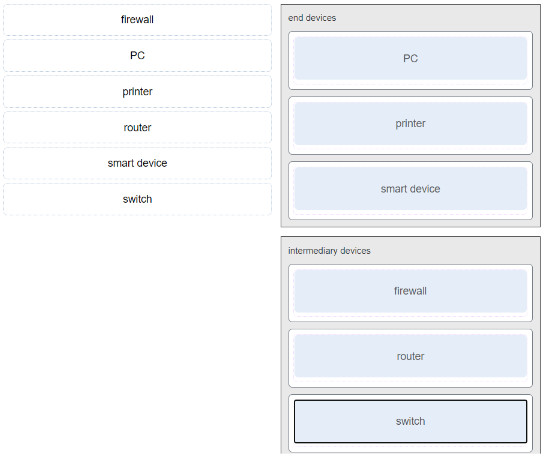
22. What is a host-based intrusion detection system (HIDS)?
- It detects and stops potential direct attacks but does not scan for malware.
- It is an agentless system that scans files on a host for potential malware.
- It identifies potential attacks and sends alerts but does not stop the traffic.
- It combines the functionalities of antimalware applications with firewall protection.
Because the HIDS runs directly on the host, itis considered an agent-based system.
23. What type of route is created when a network administrator manually configures a route that has an active exit interface?
- directly connected
- static
- local
- dynamic
24. Which characteristic describes a wireless client operating in active mode?
- must be configured for security before attaching to an AP
- broadcasts probes that request the SSID
- ability to dynamically change channels
- must know the SSID to connect to an AP
25. Which routing protocol is used to exchange routes between internet service providers?
- OSPF
- EIGRP
- ISIS
- BGP
- RIP
26. What is the first step in the CSMA/CA process when a wireless client is attempting to communicate on the wireless network?
- The client sends an RTS message to the AP.
- The client sends a test frame onto the channel.
- The client listens for traffic on the channel.
- The AP sends a CTS message to the client.
27. What Wi-Fi management frame is regularly broadcast by APs to announce their presence?
- authentication
- beacon
- probe
- association
28. What are the three parts of all Layer 2 frames? (Choose three.)
- source and destination IP address
- payload
- sequence number
- frame check sequence
- time-to-live
- header
29. What is the first step in the CSMA/CA process when a wireless client is attempting to communicate on the wireless network?
- The client sends an RTS message to the AP.
- The client sends a test frame onto the channel.
- The client listens for traffic on the channel.
- The AP sends a CTS message to the client.
30. In which memory location is the routing table of a router maintained?
- ROM
- flash
- NVRAM
- RAM
31. Lightweight access points forward data between which two devices on the network? (Choose two.)
- wireless router
- default gateway
- wireless LAN controller
- autonomous access point
- wireless client
32. A Cisco router is running IOS 15. What are the two routing table entry types that will be added when a network administrator brings an interface up and assigns an IP address to the interface? (Choose two.)
- route that is manually entered by a network administrator
- local route interface
- route that is learned via OSPF
- directly connected interface
- route that is learned via EIGRP
33. Match the secunty service with the description.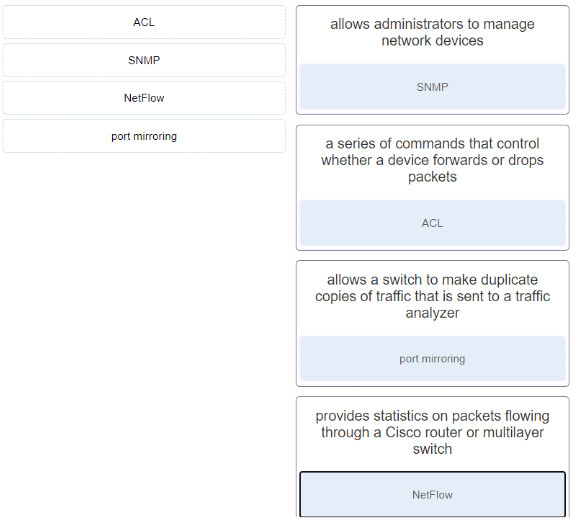
34. Match the network security device type with the descnption.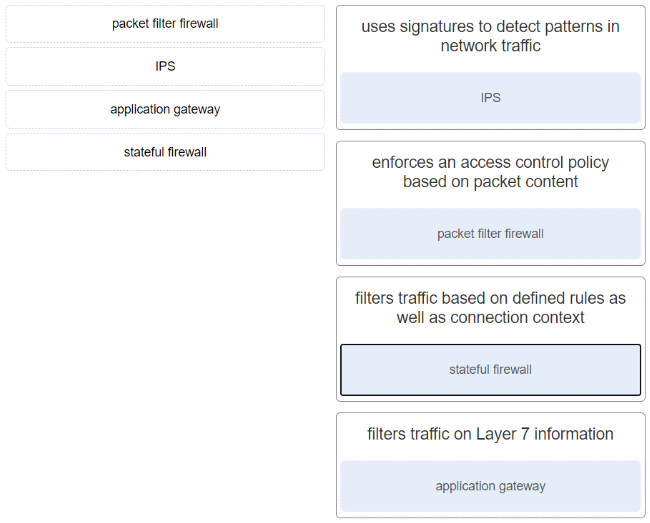
35. What Wi-Fi management frame is regularly broadcast by APs to announce their presence?
- authentication
- beacon
- probe
- association
36. What is a function of SNMP?
- synchronizes the time across all devices on the network
- captures packets entering and exiting the network interface card
- provides a message format for communication between network device managers and agents
- provides statistical analysis on packets flowing through a Cisco router or multilayer switch
37. What is a characteristic of a hub?
- operates at Layer 2
- regenerates signals received on one port out all other ports
- subdivides the network into collision domains
- uses CSMA/CA to avoid collisions
38. Match the network security device type with the description.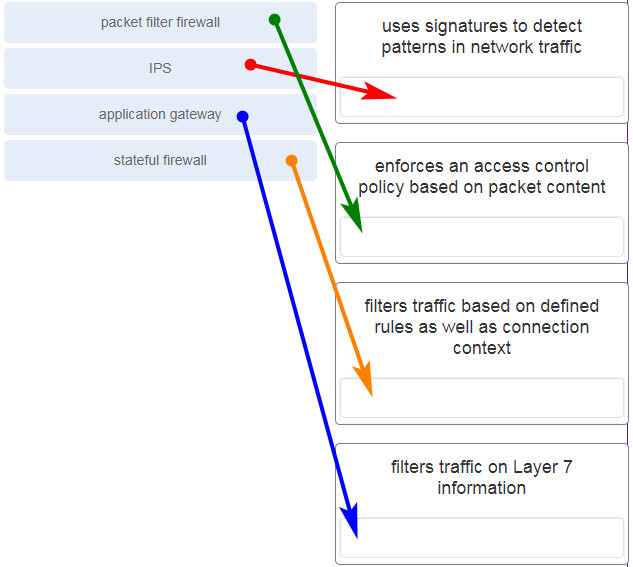
39. Which firewall feature is used to ensure that packets coming into a network are legitimate responses to requests initiated from internal hosts?
- application filtering
- stateful packet inspection
- packet filtering
- URL filtering
40. What is used on WLANs to avoid packet collisions?
- SVIs
- STP
- CSMA/CA
- VLANs
41. What information within a data packet does a router use to make forwarding decisions?
- the destination MAC address
- the destination host name
- the destination service requested
- the destination IP address