| How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank. |
|
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
|
DevNet Associate (Version 1.0) – DevNet Associate Module 4 Exam Answers
1. Refer to the exhibit. A network administrator is using a Python script to test a REST API request. The traceback message indicates that there is an error in the URI. What is a possible issue?
- The protocol is wrong.
- The query component is missing.
- The destination host address is wrong.
- The SSL certificate is invalid.
Explanation: The error message indicates “ConnectionError”. The destination host address is probably wrong because it cannot be reached.
2. Match the RESTful API method to CRUD function.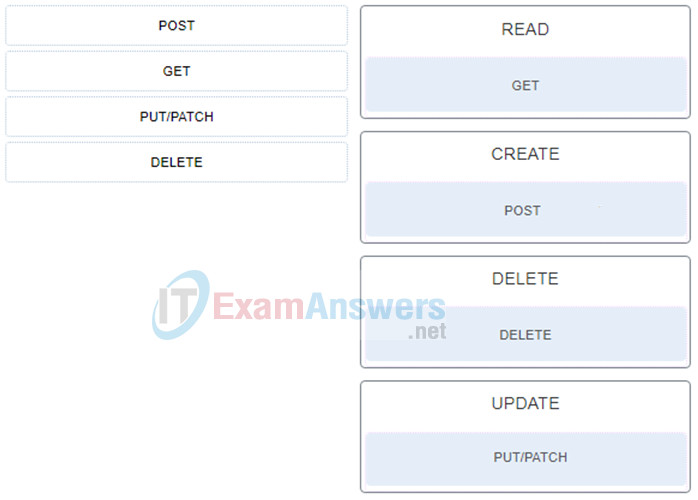
3. What is an architectural constraint to which a true RESTful API web service must adhere?
- It operates in a stateless way.
- It uses HTTPS to transport data.
- It must operate along with a DNS server.
- It operates as a cloud service.
4. Refer to the exhibit. A network administrator is using a Python script to send a REST API request. What is the purpose of the line of code resp = requests.get(url, verify = False) ?
- It bypasses the certificate validation check.
- It tests the function of the Python requests library
- It omits the sending URL in the response.
- It skips the URL verification step and tests the resource path.
Explanation: When the scheme of the URI is HTTPS, the connection performs an SSL handshake between the client and the server in order to authenticate each other. This handshake needs to be successful before the REST API request can be sent to the API server. In a development stage, APIs with HTTPS need testing and because a valid certificate is not yet obtained, the SSL handshake process can be turned off with the code line.
5. A client is sending a REST API request to a web server. The request includes the need for data compression. Which three values are acceptable for the Accept-Encoding request header? (Choose three.)
- *
- xz
- br
- gzip
- tar
- zip
Explanation: A few of the acceptable values for the Accept-Encoding request header are gzip, compress, deflate, br, identity, and *.
6. What is the meaning of the term flow as it relates to the OAuth 2.0 authorization framework?
- It is the number of requests contained in the token bucket.
- It is a process for an API request to send authentication credentials to a web service.
- It is a process for an API user to obtain an access token from the authorization server.
- It is the sequence of data exchanged between a REST API request and a response.
Explanation: Open Authorization, also known as OAuth, combines authentication with authorization. It is usually the recommended form of authentication/authorization for REST APIs. OAuth 2.0 enables preregistered applications to get authorization to perform REST API requests on behalf of a user without the user needing to share its credentials with the application itself. OAuth enables the user to provide credentials directly to the authorization server to obtain an access token that can be shared with the application. This process of obtaining the token is called a flow. The application then uses this token in the REST API as a Bearer Authentication. The web service for the REST API then checks the Authorization server to make sure the token is valid and that the requester is authorized to perform the request.
7. What is a characteristic of a RESTful API?
- It uses HTTP methods to gather and manipulate data.
- It is a southbound API.
- It facilitates the configuration changes from a network controller to end devices.
- It supports a secure data transmission between a remote user and an enterprise network.
Explanation: RESTful APIs use HTTP methods to gather and manipulate data. They are northbound APIs. Because there is a defined structure for how HTTP works, it offers a consistent way to interact with RESTful APIs from multiple vendors.
8. Which characteristic of the SOAP architecture specifies communication between all similar and dissimilar application types?
- independence
- interface uniformity
- neutrality
- extensibility
Explanation: SOAP was designed so that all types of applications can communicate with each other, no matter how dissimilar they are. The applications can be built using different programming languages, can run on different operating systems, and can be as dissimilar as possible.
9. In the REST API request URI example http://example.com/update/person?id=42&email=person%40example.com , which term describes the component example.com ?
- query
- path
- scheme
- authority
Explanation: REST API requests are essentially HTTP requests that follow the REST principles. REST API requests are made up of 4 major components, namely, Uniform Resource Identifier (URI), HTTP Method, Header, and Body. A URI is essentially the same format as a URL used in a browser to go to a web page. The syntax consists of the following components in syntax order:
Scheme – specifies which HTTP protocol should be used.
Authority – also called destination, consists of two parts, host and port.
Path – also known as resource path, specifies the location of the resource on the website.
Query – specifies query parameters with additional details for scope, for filtering, or to clarify a request.
10. Which SOAP message root element defines the XML document as a SOAP message?
- Meta tag
- Body
- Envelope
- Header
11. Which type of credential information is used for the bearer authentication in REST APIs?
- a username and password set by the client
- a password encoded using Base64
- an MD5 hash string generated by the client application
- a string generated by an authentication server
Explanation: Bearer Authentication uses a bearer token, which is a string generated by an authentication server such as an Identity Service (IdS).
12. What are two purposes for using rate limits on public and unrestricted APIs? (Choose two.)
- to avoid a server overloading from too many requests at the same time
- to limit the number of authorization requests per API call
- to provide better service and response time to all users
- to ensure a client uses a multifactor authentication mechanism
- to limit the number of passwords that a client can have in making API requests
Explanation: Using an API rate limit is a way for a web service to control the number of requests a user or application can make per defined unit of time and it is considered a best practice for public and unrestricted APIs. Some benefits of using rate limits include the following:
Avoid a server overload from too many requests at once.
Provide better service and response time to all users.
Protect against a denial of service (DoS) attack.
13. Which HTTP response status code indicates that the user is not authenticated to access the site?
- 201
- 400
- 401
- 403
- 404
Explanation: Most common HTTP status codes include the following:
- 200 – OK (using GET or POST to exchange data with an API successfully)
- 201 – Created (creating resources by using a REST API call successfully)
- 400 – Bad Request (The request from the client is failed due to client-side issue.)
- 401 – Unauthorized (The client is not authenticated to access site or API call.)
- 403 – Forbidden (The access request is not granted based on the supplied credentials.)
- 404 – Not Found (The page requested at HTTP URL location does not exist or is hidden.)
14. Which API architectural style uses an XML-based messaging protocol to communicate between applications?
- SOAP
- REST
- NFS
- XML-RPC
Explanation: Simple Object Access Protocol (SOAP) is a messaging protocol used when applications need to communicate. It is an XML-based protocol that was developed by Microsoft.
15. A network engineer is learning about Rest APIs. When executing a particular API, the server responds with curl. How is this information useful?
- Curl shows the retrieved information in JSON format.
- Curl shows how to access the content displayed in the response body using curl.
- Curl shows the information the API returned from the server.
- Curl shows the URL used in the API request.
Explanation: Clients for URLs (curl or cURL) is a tool used on many platforms for getting or sending files using URL syntax. The information returned can be copied, then used from a command prompt with the curl command to either get information using the GET parameter or send data using the POST parameter.
16. In which situation would a synchronous API be used?
- when a server is not part of the process
- when the original API request or data from the request is delayed
- when data is being retrieved from a database
- when the client is not required to take action
Explanation: Synchronous APIs respond to a request directly and immediately such as when data is being provided from memory or a database. In contrast, asynchronous APIs may send a notification that a data request has been made, send the data later, trigger a callback to provide the data, or process the request and then take an appropriate action. The action can be immediate, but it does not have to be.